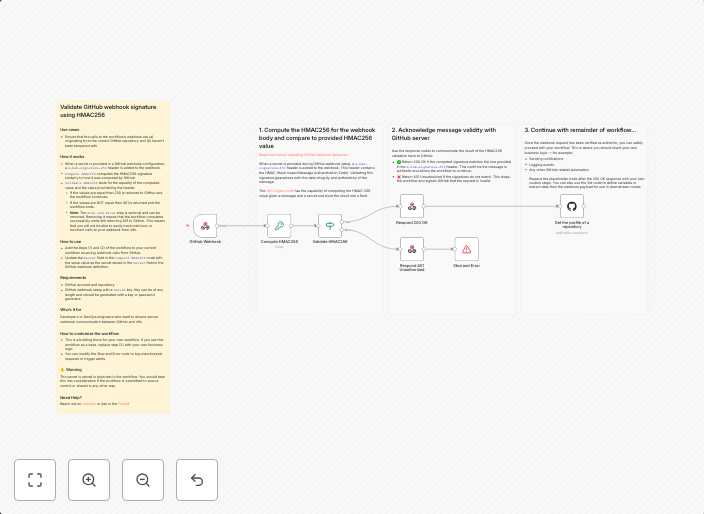
Secure GitHub webhooks with HMAC256 signature validation
Use cases Ensure that the calls to the workflow's webhook are (a) originating from the correct GitHub repository and (b) haven't been tampered with. How it...
Get This WorkflowAbout This Workflow
What This Workflow Does
This n8n automation workflow secures GitHub webhooks by validating the HMAC256 signature of incoming webhook requests. This ensures that the calls to the workflow's webhook are originating from the correct GitHub repository and haven't been tampered with. By doing so, it prevents potential security risks and ensures that only authorized requests are processed.
Who Should Use This
Developers and DevOps teams working with GitHub webhooks should consider using this workflow to enhance their integration security.
Key Features
- Validates HMAC256 signature of incoming GitHub webhook requests
- Ensures requests originate from the correct GitHub repository
- Prevents tampered requests from being processed
- Enhances overall security of GitHub webhooks
How to Get Started
To use this workflow, simply import it into your n8n instance and set up the necessary credentials for your GitHub repository. Adjust the workflow settings according to your specific requirements.
Use This Workflow in n8n →Similar Workflows
Affiliate Disclosure: We may earn a commission if you sign up for n8n through our links. This doesn't affect our recommendations.